The study involved significant activities in estimating the current market size for the Middle East cybersecurity market. Exhaustive secondary research was done to collect information on the Middle East's cybersecurity industry. The next step was to validate these findings, assumptions, and sizing with industry experts across the value chain using primary research. Different approaches, such as top-down and bottom-up, were employed to estimate the total market size. After that, the market breakup and data triangulation procedures were used to estimate the market size of the segments and sub-segments of the Middle East cybersecurity market.
Secondary Research
The market for the companies offering Middle East cybersecurity market solutions and services is arrived at by secondary data available through paid and unpaid sources, analyzing the product portfolios of the major companies in the ecosystem, and rating the companies by their performance and quality. Various sources were referred to in the secondary research process to identify and collect information for this study. The secondary sources include annual reports, press releases, investor presentations of companies, white papers, journals, certified publications, and articles from recognized authors, directories, and databases.
In the secondary research process, various secondary sources were referred to for identifying and collecting information related to the study. Secondary sources included annual reports, press releases, and investor presentations of the Middle East cybersecurity market vendors, forums, certified publications, and whitepapers. The secondary research was used to obtain critical information on the industry's value chain, the total pool of key players, market classification, and segmentation from the market and technology-oriented perspectives.
Primary Research
In the primary research process, various supply and demand sources were interviewed to obtain qualitative and quantitative information for this report. The primary sources from the supply side included industry experts, such as Chief Executive Officers (CEOs), Vice Presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various key companies and organizations operating in the Middle East cybersecurity market.
After the complete market engineering (calculations for market statistics, market breakdown, market size estimations, market forecasting, and data triangulation), extensive primary research was conducted to gather information and verify and validate the critical numbers arrived at. Primary research was also undertaken to identify the segmentation types, industry trends, competitive landscape of Middle East cybersecurity solutions offered by various market players, and fundamental market dynamics, such as drivers, restraints, opportunities, challenges, industry trends, and key player strategies.
In the complete market engineering process, the top-down and bottom-up approaches and several data triangulation methods were extensively used to perform the market estimation and market forecasting for the overall market segments and subsegments listed in this report. Extensive qualitative and quantitative analysis was performed on the complete market engineering process to list the key information/insights throughout the report.
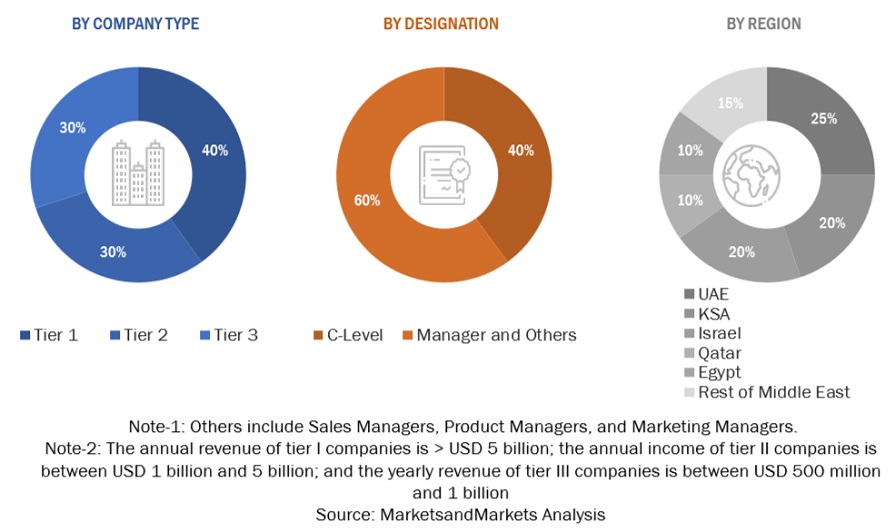
Following is the breakup of the primary study:
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Top-down and bottom-up approaches were used to estimate and validate the size of the Middle East cybersecurity market and the size of various other dependent sub-segments in the overall Middle East cybersecurity market. The research methodology used to estimate the market size includes the following details: critical players in the market were identified through secondary research, and their market shares in the respective regions were determined through primary and secondary research. This entire procedure included the study of the annual and financial reports of the top market players, and extensive interviews were conducted for key insights from the industry leaders, such as CEOs, VPs, directors, and marketing executives.
All percentage splits and breakdowns were determined using secondary sources and verified through primary sources. All possible parameters that affect the market covered in this research study have been accounted for, viewed in extensive detail, verified through primary research, and analyzed to get the final quantitative and qualitative data. This data is consolidated and added to detailed inputs and analysis from MarketsandMarkets.
INFOGRAPHIC DEPICTING BOTTOM-UP AND TOP-DOWN APPROACHES
To know about the assumptions considered for the study, Request for Free Sample Report
Data Triangulation
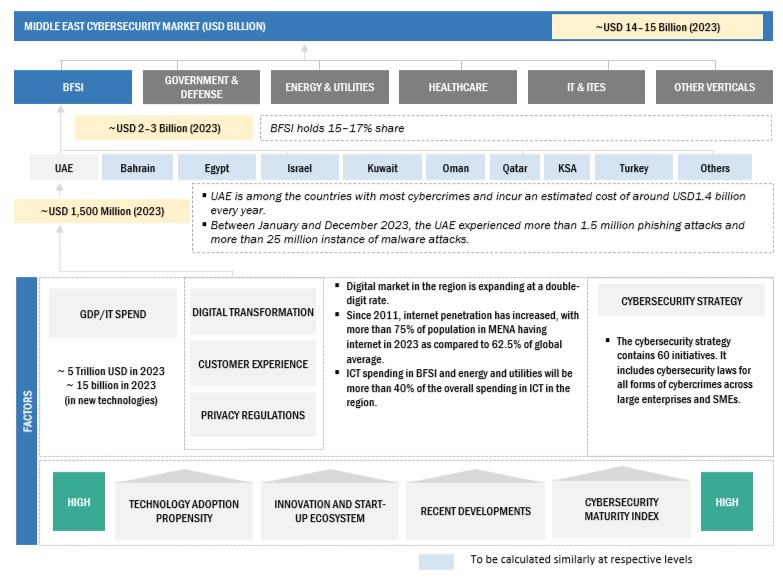
The market was split into several segments and subsegments after arriving at the overall market size using the market size estimation processes explained above. The data triangulation and market breakup procedures were employed, wherever applicable, to complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment. The data was triangulated by studying various factors and trends from both the demand and supply sides.
Market Definition
According to MarketsandMarkets, cybersecurity is a set of technologies, processes, and practices to fortify critical systems, such as networks, physical devices, programs, and information, from unauthorized access, insider threats, and malicious attacks. These cyberattacks can affect data transmission across the networks, cause operational disruptions, and result in money extortion/ransomware. Cybersecurity, or information security, can be provided through hardware, software, and services.
In the Middle East region, evolving developments in digitalization initiatives, growing impact of Gen AI, and growing exposure to sophisticated cyberattacks are the major factors for adopting cybersecurity solutions and services. Countries across the region are establishing national cybersecurity strategies and critical information infrastructure protection policies to safeguard the protection of vital digital assets.
Key Stakeholders
-
Chief technology and data officers
-
Consulting service providers
-
Managed security services professionals
-
Business analysts
-
Information Technology (IT) professionals
-
Government agencies
-
Investors and venture capitalists
-
Small and Medium-sized Enterprises (SMEs) and large enterprises
-
Third-party providers
-
Consultants/consultancies/advisory firms
-
Managed and professional service providers
Report Objectives
-
To describe and forecast the Middle East cybersecurity market by offering, solution type, security type, deployment mode, organization size, vertical, and region from 2023 to 2028, and analyze the various macroeconomic and microeconomic factors that affect market growth
-
To analyze the subsegments of the market concerning individual growth trends, prospects, and contributions to the overall market
-
To provide detailed information regarding major factors (drivers, restraints, opportunities, and challenges) influencing the growth of the market
-
To analyze the opportunities in the market for stakeholders and provide details of the competitive landscape for the major players
-
To profile the key market players; provide a comparative analysis based on the business overviews, regional presence, product offerings, business strategies, and critical financials; and illustrate the market's competitive landscape.
-
To track and analyze the competitive developments, such as mergers and acquisitions, product developments, partnerships and collaborations, and research development (R&D) activities, in the market
Customization Options
With the given market data, MarketsandMarkets offers customizations based on company-specific needs. The following customization options are available for the report:
Geographic Analysis
-
Further breakup of the Middle Eastern market into countries contributing 75% to the regional market size
Company Information
-
Detailed analysis and profiling of additional market players (up to 5)



Growth opportunities and latent adjacency in Middle East Cybersecurity Market