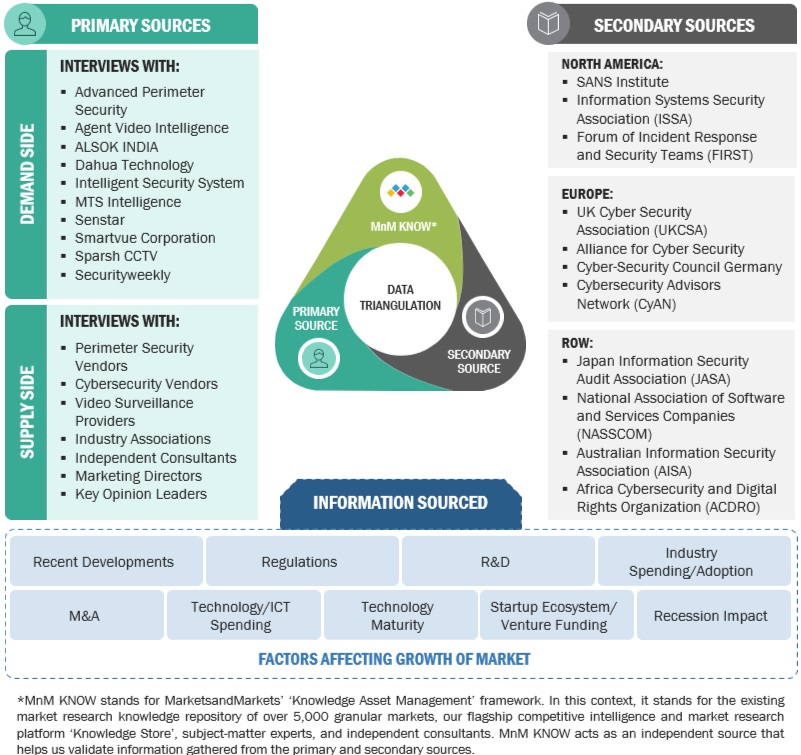
The study involved significant activities in estimating the current market size for Perimeter Security. Intensive secondary research was conducted to collect information about perimeter security and related ecosystems. The industry executives validated these findings and assumptions and sized them across the value chain using a primary research process as a next step. Top-down and bottom-up market estimation approaches were used to estimate the market size globally, followed by the market breakup and data triangulation procedures to assess the market segment and sub-segments in perimeter security.
Secondary Research Process:
Various sources were referred to in the secondary research process to identify and collect perimeter security information. These sources include annual reports, press releases, perimeter security software and service vendor investor presentations, forums, vendor-certified publications, and industry/association white papers. These secondary sources were utilized to obtain critical information about perimeter security’s solutions and services supply & value chain, a list of 100+ key players and SMEs, market classification, and segmentation per the industry trends and regional markets. The secondary research also gives us insights into the key developments from market and technology perspectives, which primary respondents further validated.
The factors considered for estimating the regional market size include technological initiatives undertaken by governments of different countries, GDP growth, ICT spending, recent market developments, and market ranking analysis of primary perimeter security solutions and service vendors.
Primary Research Process:
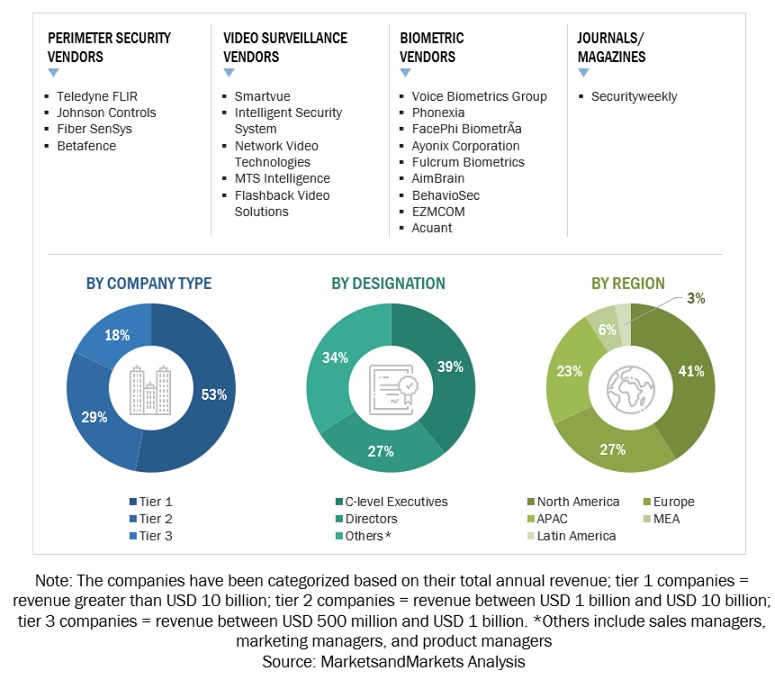
We have conducted primary research with industry executives from both the supply and demand sides. The primary sources from the supply side include chief executive officers (CEOs), vice presidents (VPs), marketing directors, and technology and innovation executives of key companies operating in the perimeter security market. We have conducted primary interviews with the executives to obtain qualitative and quantitative information for perimeter security.
The market engineering process implemented the top-down and bottom-up approaches and various data triangulation methods to estimate and forecast the market segments and subsegments. During the post-market engineering process, we conducted primary research to verify and validate the critical numbers we arrived at. The primary analysis was also undertaken to identify the segmentation types, industry trends, the competitive landscape of the perimeter security market players, and fundamental market dynamics, such as drivers, restraints, opportunities, challenges, industry trends, and key strategies.
Following is the breakup of the primary research:
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation Process:
Both top-down and bottom-up approaches were implemented for market size estimation to estimate, project, and forecast the size of the global and other dependent sub-segments in the overall perimeter security market.
The research methodology used to estimate the market size includes these steps:
-
The key players, SMEs, and startups were identified through secondary sources. Their revenue contributions in the market were determined through primary and secondary sources.
-
Annual and financial reports of the publicly listed market players were considered for the company’s revenue details, and,
-
Primary interviews were also conducted with industry leaders to collect information about their companies, competitors, and key players in the market.
-
All percentage splits, and breakups were determined using secondary sources and verified through primary sources.
Top-down and Bottom-up Approach
To know about the assumptions considered for the study, Request for Free Sample Report
Data Triangulation
Data triangulation is a crucial step in the market engineering process for perimeter security. It involves utilizing multiple data sources and methodologies to validate and cross-reference findings, thereby enhancing the reliability and accuracy of the market segment and subsegment statistics. To conduct data triangulation, various factors and trends related to the perimeter security market are studied from both the demand and supply sides. It includes analyzing data from diverse sources such as market research reports, industry publications, regulatory bodies, financial institutions, and technology providers. By examining data from different perspectives and sources, data triangulation helps mitigate potential biases and discrepancies. It provides a more comprehensive understanding of the market dynamics, including the size, growth rate, market trends, and customer preferences.
Furthermore, data triangulation aids in identifying any inconsistencies or outliers in the data, enabling researchers to refine their analysis and make informed decisions. It strengthens the credibility of the market engineering process by ensuring the conclusions drawn are based on robust and corroborated data. Data triangulation is a rigorous and systematic approach to enhancing the reliability and validity of market segment and subsegment statistics in perimeter security. It provides a solid foundation for informed decision-making and strategic planning within the industry.
Market Definition
Perimeter security refers to the systems and measures implemented to protect an area or property by preventing unauthorized access and detecting intrusions across its boundaries. It is a form of security encompassing physical barriers such as fences, gates, walls, and technological systems, including video surveillance, intrusion detection sensors, access control, and alarms. These components safeguard critical infrastructures, commercial properties, residential areas, and governmental facilities from external threats. Perimeter security solutions are essential in identifying potential security breaches and enabling timely responses to protect people, property, and assets within a designated perimeter.
Key Stakeholders
-
Government agencies
-
Perimeter security vendors
-
Independent software vendors
-
Consulting firms
-
System integrators
-
Value-added resellers (VARs)
-
Information technology (IT) security agencies
-
Managed security service providers (MSSPs)
-
Raw material/component suppliers
-
Research organizations and consulting companies
-
Government bodies, such as regulating authorities and policymakers
-
Venture capitalists and private equity firms
Report Objectives
Customization Options
With the given market data, MarketsandMarkets offers customizations based on company-specific needs. The following customization options are available for the report:
Geographic Analysis
Company Information
-
To define, describe, and forecast the perimeter security market based on component, system, service, end-use sector, and region:
-
To predict and estimate the market size of five central areas: North America, Europe, Asia Pacific, Middle East & Africa, and Latin America
-
To analyze the subsegments of the market concerning individual growth trends, prospects, and contributions to the overall market
-
To provide detailed information related to the primary factors (drivers, restraints, opportunities, and challenges) influencing the growth of the perimeter security market
-
To analyze opportunities in the market for stakeholders by identifying high-growth segments of the perimeter security market
-
To profile the key players of the perimeter security market and comprehensively analyze their market size and core competencies.
-
Track and analyze competitive developments, such as new product launches, mergers and acquisitions, partnerships, agreements, and collaborations in the global perimeter security market.
-
Further breakup of the Asia Pacific market into countries contributing 75% to the regional market size
-
Further breakup of the North American market into countries contributing 75% to the regional market size
-
Further breakup of the Latin American market into countries contributing 75% to the regional market size
-
Further breakup of the Middle Eastern and African market into countries contributing 75% to the regional market size
-
Further breakup of the European market into countries contributing 75% to the regional market size
-
Detailed analysis and profiling of additional market players (up to 5)



Growth opportunities and latent adjacency in Perimeter Security Market